The year 2018 started out with concerning news for all users of technology,
but especially so for the embedded developer tasked with securing their
designs. If the information about new attack methods versus high end
processing units is any indication of today’s threat landscape, there
is a long and uphill run in store. To address security needs of today’s
embedded designs, it takes more than the knowledge of hardware and software.
There are other skills and methods needed to ensure secure development,
manufacturing and deployment of devices. The reality is that there is no
simple answer, turnkey solution or magic spell to fix the end-to-end security
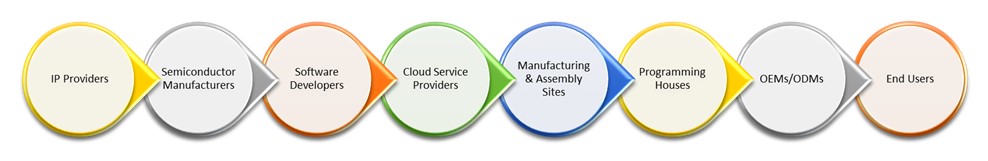
flaws already built into our embedded world. There should be no doubt that in
the present age, the responsibility of secure embedded design does not rest
solely on the shoulders of just one entity, but on all who are involved in the
creation of the end devices. All players mentioned below must contribute to
the end-to-end security of devices in IoT applications.
What do we do? Faced with such a daunting task many may stall or concede. But
by no means should we give up or put off addressing the need for end-to-end
security. So, one practical and achievable step is working to design a secure
and trusted boot on the main processing unit in your device. This is an
essential undertaking for anyone working to meet their security goals. To
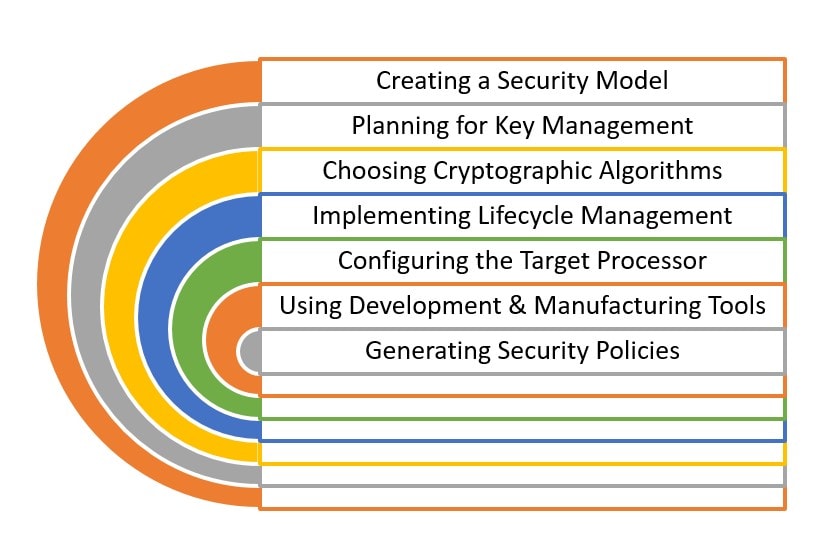
tackle the secure boot design, the embedded system developer must address the
following topics:
A secure boot design protects against a wide range of attack scenarios.
Whether it be focused attacks as described
here, or remote attacks against firmware updates or even a future scenario that
we are not yet aware. The act of authenticating application code before
allowing it to run is an essential component of end-to-end security. The NXP
IoT and Security Solutions team has been building up resources including
webinars, whitepapers and hands-on courses for users of the broadly deployed
Kinetis MCU product line to address these topics. Please follow the links or
see the resources section to learn more. In addition, the
SLN-POS-RDR
secure card reader solution delivers a secure boot implementation built into
the software package, along with the hardware and certification collateral.
Are you already implementing a secure boot into your designs today?
If not, do you plan to retrofit this essential feature into your deployed
devices?
Will you work to achieve a secure boot in your next design?
Please comment and answer these questions on my blog.
Resources:
On-Demand Security Webinar Series:
Hands-On:
Payment Solutions – Secure Boot Lab Guide
Whitepaper: Prevent edge node attacks by securing your firmware






