The secure boot, or the authentication of application software upon every
system start up is an essential component for the IoT design. It provides many
advantages for protecting the embedded system. For one, it is the basis for
securing the integrity of application code, and any firmware update.
Importantly, if an attacker manages to insert their software on the system,
with a secure boot flow, the device can recover to a known good state. NXP has
a mission to propagate this technology to every embedded developer and for
every embedded design.
A big step toward the democratization of secure boot — the capabilities
integrated into NXP’s Crossover MCU family, the i.MX RT. The
i.MX RT
integrates the advanced Arm® Cortex®-M7 core to provide a highly
capable microcontroller built on a processor chassis. With the i.MX RT
and its associated software and tools for secure boot, common barriers
for achieving end-to-end security have been removed.
As shown in the architecture diagram, the i.MX RT
brings the essential security components together for the embedded designer.
Secure development including an authenticated boot flow with the i.MX RT
leverages years of experience gained from its applications processor lineage.
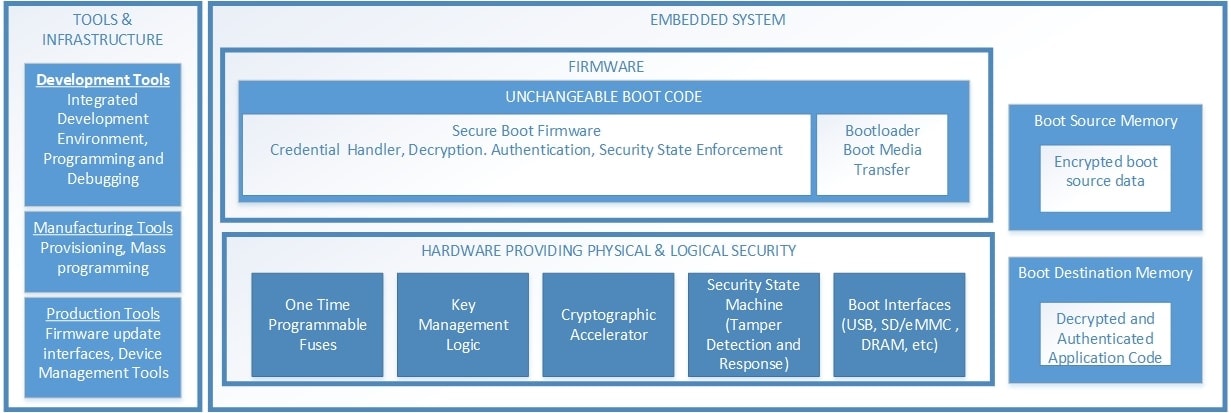
The ROM firmware enabling the secure boot, as well as the tools used in the
development and manufacturing processes, have been commercially used and
tested. For more details, have a look at the recently released
white paper.
With the technology in place, the secure boot is achievable, but there is
always more that can be done to enable secure boot for every design.
That is why across the world, the topic of secure boot has been or will be
presented to participants in
NXP’s Technology Day events

In some cases secure boot hands-on classes have been held to propagate the
understanding of the technology. The resources associated with these classes
are posted for the
embedded community.
With the white paper, lab guides and continued focus on the secure boot
capabilities, the goal of democratization of secure boot is achievable. Please
don’t hesitate to start your security integration with the latest
processors and enablement.






